Why UK Businesses Choose HID Key Fob Readers for Secure Access
Access control is evolving fast in the UK. For facilities from small offices to multi-site campuses, choosing the right hardware and management strategy is critical. In this guide we explain why a hid key fob reader remains a practical, secure, and cost-effective option for many organizations, how it integrates with modern cloud solutions and what IT teams should consider when specifying and deploying readers for their sites.
What is a hid key fob reader?
A hid key fob reader is a proximity device that reads contactless credentials—usually low-frequency or smart-card formats—attached to an employee’s keys. Readers vary from compact mullion units to versioned smart readers with PIN pads, Bluetooth or mobile credential support. In the UK market, major vendors like HID Global supply a wide range of certified readers and credentials for diverse use cases.
Security benefits and why they matter in the UK

Physical access control is the first line of defence. When paired with policy-driven management, a hid key fob reader reduces tailgating risks, supports rapid credential revocation when items are lost, and can be combined with two-factor authentication for higher-security areas. Modern readers support encrypted credential formats and mutual authentication between the reader and the back-end controller, closing several common attack vectors. For organizations subject to UK regulations and standards, robust control over door events and audit trails is essential for compliance and incident response.
Integrating readers with cloud security access control solutions
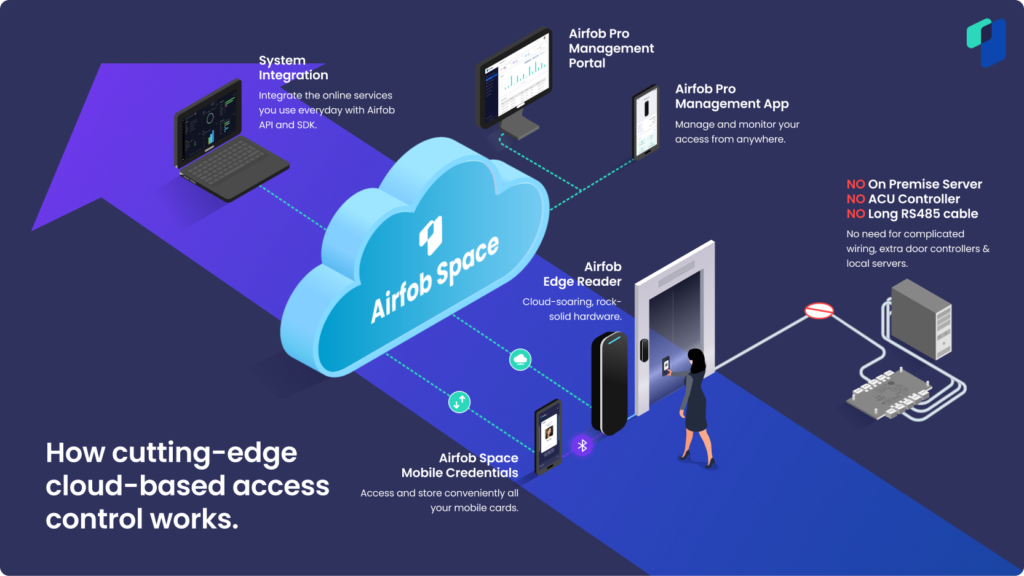
The shift to cloud security access control platforms brings centralised policy, remote management and real-time reporting to traditional access hardware. A hid key fob reader can connect to a cloud-enabled access control gateway or work through hybrid controllers that sync credentials and rules to a central console. This model reduces on-site infrastructure, speeds up onboarding of staff and contractors, and lets security teams apply consistent policies across multiple UK sites.
Cloud platforms also provide analytics and anomaly detection—useful for spotting suspicious patterns such as repeated failed reads or access attempts outside normal hours. When selecting a cloud partner, verify data residency, encryption, and support for industry-standard integrations so your hid key fob reader investment remains future-proof.
Deployment best practices for UK facilities
Start with a site survey: map doors, expected footfall, environmental risks and mounting options. Choose reader models rated for the environment—mullion, keypad or IP67-rated readers for exposed locations. Ensure credential lifecycle policies are defined: issue, renew, suspend and revoke. For a smooth rollout, pilot the hid key fob reader on a subset of doors and validate read ranges, firmware compatibility and integration with building management systems. Train security and reception staff on credential provisioning and incident procedures. Finally, schedule firmware updates and patch management to mitigate newly discovered vulnerabilities.
Cost considerations and return on investment
Initial costs cover readers, controllers, credentials and installation. However, lifecycle benefits—reduced locksmith calls, simplified credential management and faster onboarding—often deliver strong ROI. A hid key fob reader is typically cheaper per user than biometric systems and avoids many privacy concerns. For multi-site UK operations, centralised cloud security access control lowers total cost of ownership by reducing local IT support needs.
Choosing a UK vendor and support partner
Buy from reputable vendors or certified resellers who provide local support, warranty and integration services. Look for HID Global partners and installers experienced with municipal, educational and commercial deployments. Check references and request a staged proposal that includes a proof-of-concept using your existing doors and IT infrastructure. A strong service agreement should include response SLAs, replacement policies and firmware lifecycle management.
FAQ – Common questions UK buyers ask
Q: How do I know which hid key fob reader suits my door?
A: Consider the mounting type, read range and environment. A standard mullion reader works well for office doors; an IP-rated reader is better for exposed or industrial entrances. If you require staff authentication with a PIN, choose a reader with a keypad or support for mobile credentialing alongside the hid key fob reader.
Q: Can a hid key fob reader be cloned or spoofed?
A: Older 125 kHz prox formats are more susceptible to cloning. Choose encrypted credentials and modern reader firmware, or migrate to smart-card formats that support mutual authentication to reduce spoofing risk with your hid key fob reader.
Q: How quickly can we onboard 100 staff?
A: With cloud security access control and batch provisioning, onboarding can be completed in hours rather than days. Use temporary credentials for contractors and automate expiry policies when working with a hid key fob reader ecosystem.
Short UK case study
A mid-sized London consultancy replaced legacy mechanical locks across a three-floor office with a hybrid cloud solution. The rollout used a mix of keypad readers, door controllers and 500 HID Prox credentials. The HID partner configured the system so HR could self-provision or revoke access during offboarding. Within six months, locksmith call-outs dropped by 70% and the security team reported faster investigations thanks to central logs fed from each hid key fob re
Maintenance checklist and long-term care
Regular maintenance keeps your access hardware reliable and reduces downtime. Establish a quarterly inspection routine that checks mounting brackets, weather seals and cable terminations. Review event logs monthly for anomalous patterns such as repeated failed reads or unexpected door-open events outside work hours. Keep a firmware inventory and apply vendor-recommended updates during agreed maintenance windows; test updates in a staging environment before broad deployment.
Replace worn credentials and update badge prints to reflect staff changes. Maintain spare units and standardize on a small set of models to ease support and spare parts management. For sites with high footfall, plan for more frequent inspection and cleaning to prevent degradation from dust and grime. Finally, document all changes in a central configuration repository so that audits and continuity planning are straightforward for future teams.
Also, verify that your identity and access policies align with HR workflows to speed up credential issuance. Train staff on lost-credential procedures and run an annual access review to remove dormant accounts. These steps ensure the system continues to support operational needs while maintaining high security standards. Schedule periodic third-party security assessments to validate configurations and spot weaknesses before they become incidents. Keep maintenance logs accessible for compliance and operational audits. Regularly.
Conclusion
For many UK organisations, a hid key fob reader paired with a modern cloud security access control platform offers a balanced mix of security, cost-effectiveness and operational simplicity. By following best practices for deployment, lifecycle management and vendor selection, security teams can deliver a robust, auditable access control solution that scales with the business.

