Smarter Security Starts Here: HID Card Access Control Systems
In today’s security-conscious UK workplace, choosing the right access control solution is crucial. This guide explains why the hid card access control system is a reliable, scalable, and future-ready choice for offices, schools, hospitals, and industrial sites. We’ll cover technology types, real-world benefits, migration tips, and how XS Controls can help you deploy a solution tailored to UK compliance and operational needs.
What is an HID card access control system?

An hid card access control system uses secure smart cards, proximity credentials, or mobile tokens to grant authorised entry. HID Global, a market leader, produces a broad range of credentials and readers—from classic prox cards to iCLASS SE and Seos smart cards and HID Mobile Access. These systems authenticate users, log events, and integrate with CCTV, alarms, and time & attendance platforms.
Why UK organisations choose HID
UK organisations pick HID solutions because HID access control products combine robust encryption, vendor longevity, and integration flexibility. Whether you need a small office setup or a campus-wide deployment, an HID card access control scales with minimal disruption. HID access control also supports migration paths away from legacy Wiegand systems to more secure, IP-enabled architectures.
Key components and technologies
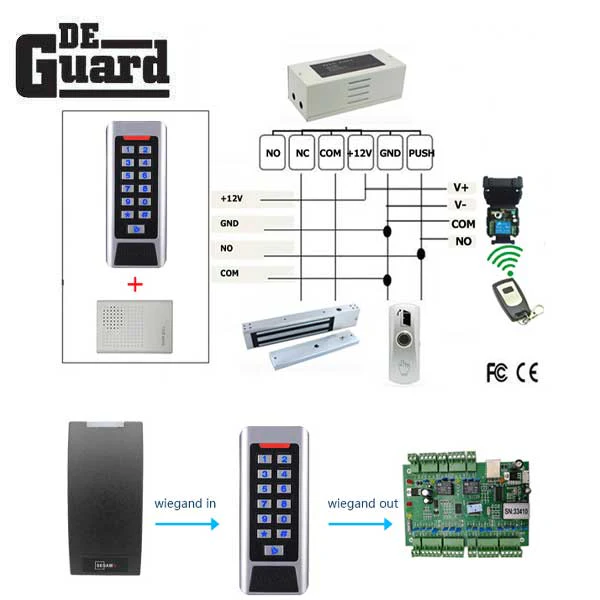
A typical HID access control deployment includes readers, controllers, credentials, and management software. HID readers come in touchless Signo, iClass SE, and multi-technology models. Credentials range from HID proximity cards and smart cards to mobile credentials. An HID card access control system often uses encrypted communication and mutual authentication to prevent cloning and replay attacks.
Security and compliance considerations
For UK businesses handling sensitive data, choose HID products that support secure element credentials and encrypted channels. An HID card access control provides audit trails for GDPR and internal security policies. Regular firmware updates and lifecycle management are essential—HID access control manufacturers publish patches and migration guides to keep installations secure.
Migrating from legacy systems
Many UK sites still use legacy prox cards and Wiegand wiring. A phased approach lets organisations adopt an HID card access control system without ripping out existing infrastructure. Hybrid readers that accept both legacy and modern credentials help maintain operations while upgrading. Partnering with an installer experienced in HID access control ensures smooth migration and minimal downtime.
Benefits for facilities managers
Facilities teams appreciate how an HID card access control centralizes access lists, simplifies lost-card management, and reduces tailgating risk through combined reader and turnstile integrations. HID access control systems improve operational efficiency by integrating with building management and visitor systems, providing a single pane of glass for security operations.
Mobile credentials and the future
HID Mobile Access provides a user-friendly alternative to physical cards. Users can authenticate with smartphones, delivering convenience while maintaining security. Integrating mobile with an HID card access control enables contactless entry, enhances hygiene, and lowers long-term card issuance costs, which is attractive to UK organisations aiming to modernise.
Cost and procurement in the UK
Total cost depends on reader types, controllers, and credential choices. An HID card access control system may have higher upfront costs than basic proximity systems but delivers lower lifecycle cost through reduced card issuance, better integration, and stronger security. XS Controls can provide UK-specific quotations, VAT-compliant procurement, and guidance on OJEU or public-sector tendering when required.
Choosing the right installer
Work with an accredited HID partner who understands local UK building regulations, data protection, and fire safety. A certified installer will ensure your HID card access control system meets operational requirements and aligns with insurance and regulatory expectations. XS Controls offers full design, installation, and post-install support across the UK.
Case studies and real-world use
From university campuses to distributed retail estates, organisations adopting an HID card access control system report fewer security incidents, faster onboarding, and easier audits. Combining readers, mobile credentials, and analytics produces actionable insights for security teams, while HID access control’s ecosystem supports third-party integrations.
FAQs
Is HID the same as proximity cards? HID makes prox cards but also produces advanced smart credentials; an HID card access control system can support both.
Can I use phones instead of cards? Yes—HID Mobile Access works alongside traditional cards in an HID access control deployment.
How long does installation take? Timelines vary; a small office can be done in days, larger sites may take weeks, especially with a phased migration to an HID card access control system.
Next steps for UK businesses
If you’re evaluating options, request a site survey from XS Controls. We’ll assess your current setup, propose an HID card access control system tailored to your security profile, and supply a clear migration and pricing plan. Contact XS Controls today to secure your premises with proven HID access control technology.
An hid card access control system delivers encrypted credentials, centralised logs, and mobile integration for modern sites. An hid card access control system delivers encrypted credentials, centralised logs, and mobile integration for modern sites. An hid card access control system delivers encrypted credentials, centralised logs, and mobile integration for modern sites. An hid card access control system delivers encrypted credentials, centralised logs, and mobile integration for modern sites.
Schedule regular audits and firmware updates to reduce vulnerabilities and ensure continued compliance with UK regulations. Maintain secure credential lifecycle management. Train staff on security policies, lost card procedures, and how to report suspicious access attempts immediately. Implement role based access with least privilege to limit exposure and simplify administration across departments and sites.
Use analytics and reporting to identify unusual patterns, late night access, or repeated failed authentication attempts for review. Test backups and incident response plans annually so your team can react quickly to breaches or system failures. Coordinate with IT and estates teams when integrating access control with CCTV, fire systems, or building management platforms. Budget for replacement credentials and periodic hardware refreshes so the HID solution remains supported and performant over time. Contact XS.

